Chinese security camera maker exposed in security farce
OK, security is hard. That's a given, and it's taking time for companies to come to grips with this fact. There has been a great deal of progress in recent years, though. Larger tech firms are starting to design for security, push updates are becoming more common and widely accepted, and device vendors are beginning to make an effort....some of them anyway.
Researchers at security firm Bitdefender have release a report on a particularly interesting case of lax security. Poking around the net using Shodan, the search engine for IoT devices, some interesting results turned up for some IP camera models from Chinese electronics manufacturer Shenzhen Neo Electronics. These guys produce a range of commodity security gear (cameras, alarms, and sensors). It seems a couple of models, known as the NIP-22 and the iDoorbell, where showing a little too much skin. Both HTTP and RTSP were exposed to the internet from between 100,000 and 140,000 devices (depending on the time of the scan).
Now that shouldn't be, you might say. You'd be right. Typically, if you want to connect your device to a service to make it remotely accessible, you send heartbeat packets out FROM the device to a central server using a secure channel. HTTPS/TLS is fine. Doing this the device establishes a return mapping through any NAT routers between it and the server, and ONLY the server. You then offer a secure connection to the server for your customers to access their iThingy and view video or adjust settings, whatever.
Shenzhen Neo Electronics didn't want to be bothered with such technicalities though, so they just have the cameras use UPnP to open the ports in your router's firewall.....job done. So, if you have one of these babies on your network, anyone in the world can connect to your RTSP service and enjoy the show.
But wait, there's more. Making these totally exposed to the internet makes them discoverable, as the researches did with a freely available search tool. Unfortunately, the connectivity wasn't the only place where the money was being saved. A little more poking quickly uncovered the fact that the exposed services used a default username of 'user' with a password of 'user'. Aaand then they found that when submitting the credentials for authentication, the firmware plops them on the stack without any length validation. This means arbitrarily large data can be passed into the firmware to cause a stack overflow, which can then be crafted such that an attacker can execute arbitrary code on the device.
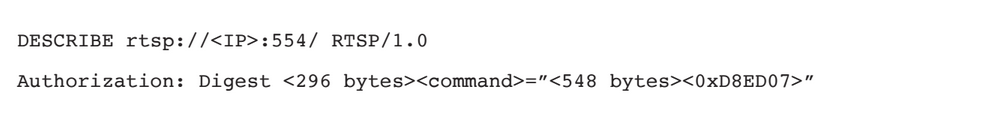
The final RTSP exploit
On top of all that, the filesystem is read/write, so once your executing code you can download your own firmware via TFTP and then force crash the device. It will dutifully restart and load whatever you want persistently. This is a case of complete ownership, easily granting a gateway into the entire internal network of the victim.
The guys at Bitdefender have only tried this on the two models stated, but they assume that the same firmware is likely used on all of Shenzhen Neo Electronics camera products, and they are most likely all vulnerable. An attempt to responsibly disclose these attacks to the manufacturer have gone completely unanswered, and even if a patch was available, the devices don't have a facility for push updates, so they will likely never be fixed.
As much as this is a hilariously epic failure worthy of a good laugh, the unpleasant fact remains that devices like these, from companies that are only interested in pumping out high-volume, low margin junk and moving on, are precisely the reason that we, and the wider internet, are all being exposed to greater risk of bot attacks.