How strong does your Wi-Fi password need to be?
Regardless of what you may think about your appeal as a hacking target, cyber security is a real issue for everyday people in the 21st century. Whether it be organized criminals wanting to profit off your identity and empty your bank accounts, or some vindictive script kiddie wanting to mess with your life over some perceived online slight, we have a responsibility to protect ourselves and our family’s information.
The subject of home cyber security could take us in many directions, but as our homes become increasingly wireless it seems like a good time to revisit the first line of defense. You’re front door, and the key used to open it, is now your Wi-Fi network and it’s authentication process.
You might say that’s all well and good, but what use is the hassle of a strong complex password if the system can be hacked regardless. The good news is that the current wireless security standards are still reasonably robust, but that concern is valid, so we should stake a look at the state of play first.
Wi-Fi Vulnerabilities
There is one wireless feature that should absolutely be disabled on any router that still offers it. WPS, or Wi-Fi Protected Security, is a standard that was introduced to make it easy for folks to join the default Wi-Fi network of their fancy new router. The problem is that the standard was poorly designed, and the 8 digit PIN that is provided to connect to the network can actually be split in half and guessed as two 4 digit PINS.
As a 4 digit PIN only has 10,000 possible combinations, this can be brute forced trivially. Rest assured that any newer routers won’t even support this, thankfully, but don’t take any chances. Check your router settings, and make sure to turn it off if it’s there.
The next point of attack would be the authentication to the network. This is the algorithm that defines how passwords are handled and what encryption is used between devices, which in turn allows communication on the network. There have been a handful of accepted standards in the life of the common Wi-Fi protocol (IEEE 802.11), notably WEP and WPA. Both WPA and the older WEP protocol are open to attack. The level of difficulty is what matters though. WEP is fundamentally flawed, and with the use of freely available tools on the internet can be broken in a matter of seconds.
WAP and WPA2 have the option of two security mechanisms to manage keys and encryption, TKIP and PSK-AES. TKIP is vulnerable to a packet injection attack, and is considered legacy as it was only created to provide an upgrade path for WEP devices. It has since been deprecated, and should not be used if your router offers it. Unfortunately PSK also has issues which can be exploited using the KRACK attack.
The newer WPA3 changed the mechanism in response, mandating the new SAE method (Simultaneous Authentication of Equals) called ‘Dragonfly’. While this did address the issues exposed by that attack, the standard included some design flaws that allowed a new attack called Dragonblood that forces devices to briefly use the older WPA2 method. WPA1 and 2 are vulnerable to a handshake capture that allows the password to grabbed and subject to a brute force attack.
Brute Force attack is the most common threat to password based security. It basically means running through a bunch of character combinations to find the one that works. This can obviously be very time consuming, so dictionary attacks are combined to speed things up.
A ‘dictionary’ in this case is a per-defined list of common passwords, dictionary words (with typical substitutions included, P@$$w0rd anyone?), and phrases that are known or thought to be used as passwords. This list can contain millions of possibilities and are constantly evolving based on leaked password databases and social trends.
Doing this on the actual network is not viable as it’s too slow. When the password can be captured during the connection phase and taken offline to work on, as with WPA1 and WPA2, an attacker they can run highly accelerated guesses on the password at their leisure. While WPA3 can be fixed with software updates, many low powered devices and cheaper brands will never get those. This is where the password strength comes in.
Password Strength
In terms of protecting against brute force attack we need to consider several elements. The search space (the number of possible characters in use), key length (how long is it), and dictionary attacks.
What the search space does is change how many combinations of characters an attacker has to guess, for each character in the password. If you only use numbers, then the search space is 10 (the digits 0 to 9), and if you only use lowercase letters, it’s 26. The key thing to remember is that any other character that you use increases the search space by a lot because an attacker doesn’t know where it was used, or how many times.
If there is a letter in there somewhere, all letters have to be checked on every character. Using all lowercase letters with a single digit in the password somewhere increases the search space to 36. Adding a capital letter increases it to 62, and so on. When multiplied by the number of characters in the password, it has an exponential effect on the number of possible guesses required.
By way of example: A 16 letter password using only lower case letters yields a brute force time of about 14 years. Adding a single upper case letter increases this to over 400,000 CENTURIES.
To see the effect of this on your passwords, you can use the free Password Haystacks tool (to see if you’re hiding your needle in the haystack of possible guesses effectively) . The effectiveness of brute forcing tools increasing rapidly with computing power, but this tool uses a very conservative estimate for the guess rate to compensate.
To be sure, base your results on the last option (Massive Cracking Array Scenario). Even today, this is an unlikely rate for real world hackers, but with dedicated FPGA cracking hardware out there. and the cheap availability of large cloud services, the guess rate is shooting up for those that have the cash.
You may be skeptical about putting your password into a webpage, but remember that the password in isolation is useless without context (what is it the password for?). Also note that the tool does not take your password anywhere. The calculations are done purely in your browser by embedded scripts. You can examine the JavaScript on the page to confirm it’s not doing anything nefarious if you wish, but I’ve already done that for you.
Alternatively, you could try this one from Experte.com which also checks to see if the password has been found in any known leaks. I haven’t examined the code for this one as yet, but keep in mind you’re only supplying an arbitrary password without any context, so it can’t be linked to any particular account.
Pracitcal Passwords
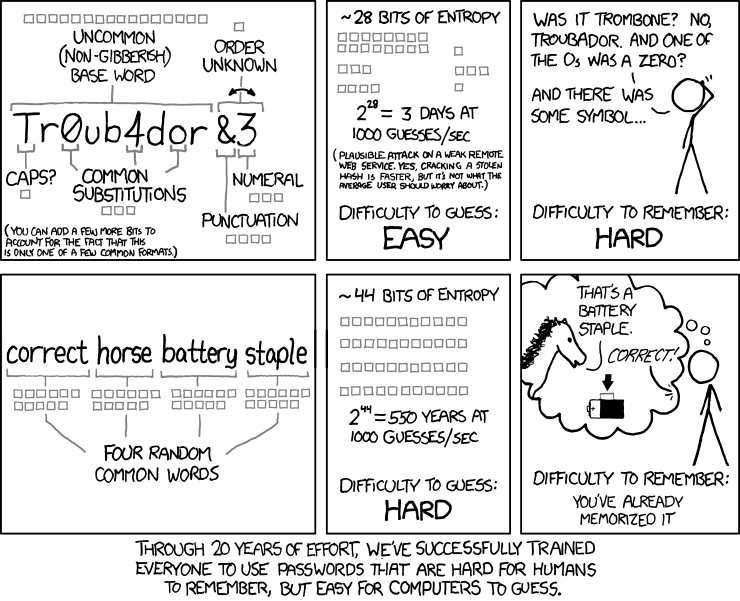
As the note on the haystacks page points out, length and a large search space are useless if the password is in a dictionary, so we need to consider what we use in the password as well. Does this mean you need a horrible long, complex, indecipherable password to be safe? Actually, no. One of the best explanations of this has been around for a while in the form of a comic from XKCD.
What this is saying, essentially, is that length is more important than funny characters. If you choose 4 or 5 memorable words and glue them together, so long as they don’t make sense together, you’ll be better off than trying to come up with something random. Of course, adding a non-alphabetic character in there anywhere will greatly protect against dictionary-based attacks as well.
Long random passwords are best, of course, but in a world where we need to be able to enter this password many times on mobile keyboards, and on-screen with remote controls (Smart TVs, DVRs, and streaming devices for example) we need something that is secure AND usable.
You’ll notice the use of the term ‘entropy’ when discussing encryption keys and passwords. This is essentially a measure of how resistant a password is to brute force guesses. Currently a password is considered strong if it has over 60 bits of entropy. This can change over time as processing power makes these guesses faster. You can check the entropy in your password (without giving up the password itself) using this handy entropy calculator.
A long multi-word passphrase, with a number and/or capital letter thrown in somewhere, will provide a high level of security which is also practical to use across all your devices.